Go vs. Python
tl;dr; It's not a competition! I'm just comparing Go and Python. So I can learn Go. So recently I've been trying to learn Go. It's a...


Reversing and Cracking first simple Program - bin 0x05
A very simple reversing challenge for Linux GitHub: https://github.com/LiveOverflow/liveo... join the discussion:...


USB Hacking with Arduino
USB devices are so common nowadays - wouldn't it be nice to use one with your homebrew electronics projects? Equipped with an Arduino...
Introduction to Use After Free Vulnerabilities
Use After Free (UAF) vulnerabilities are a class of memory corruption bug that have been very successful in the world of browser...
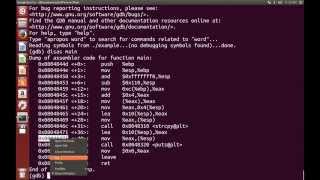

Exploiting Buffer Overflows
This tutorial goes over the basic technique of how to exploit a buffer overflow vulnerability with an example. This tutorial assumes that...


Raspberry Pi Setup
First Vlog, and attempt to setup a raspberry pi zero. Pi Zero - https://www.raspberrypi.org/products/... Pi 2 -...
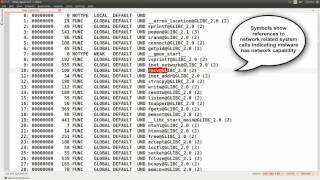

Analysis of Linux malware Tsunami using Limon Sandbox
The video demonstrates the static, dynamic and memory analysis of Linux malware Tsunami using Limon Sandbox. Limon download Link:...


How to Hack Using JavaScript (XSS, Brute Force, BeEF)
Similar to Metasploit, BeEF is a framework for launching attacks. Unlike Metasploit, it is specific to launching attacks against web...


How to Install the New Tor Browser in Kali Linux
This video covers installing the Tor Browser Bundle v3.6+ (older versions work too, there is just an extra step with the new version,) on...


